
In the modern age of technology, when most communication takes place via email, guaranteeing the security of sensitive data has become critical. With cyber risks on the rise, frequent email security checks are no longer an option—they’re a must. In this blog, we discuss the importance of Email security check and offer practical advice on how businesses can protect themselves from data leaks and breaches in 2024.
Table of Contents
ToggleWhat is a Data Leak? Why do data breaches happen?
A data leak occurs when sensitive data is exposed to someone(s) who are not authorized to see it. Data leaks can occur due to two factors: cybersecurity assaults and poor security measures.

Personal Identifiable Information (PII) is one sort of sensitive data, as is commercial data such as project plans, financial details, software code, and other comparable data.
Personal Identifiable Information (PII) refers to any data that may be used to identify an individual, such as their first and surname name, email address, phone number, passport number, driver’s licence, social security number, and other personal information.
Infected Methods That Cause Data Leaks
Attackers utilize a variety of nefarious tactics to induce data breaches. Individuals or groups utilise a variety of techniques to deceive end users into granting access to their data. Phishing attacks, malware assaults, and brute-force attacks are the three most frequent tactics.

Phishing email assaults are one of the most popular harmful approaches we encounter nowadays. According to our Cyber Security Report, phishing emails account for nearly 40% of all assaults. Viruses and other forms of malware are frequently embedded into many file formats, such as Word, Excel, PDF, and archives.
Hackers create sophisticated emails that appear like genuine things and deceive you into opening dangerous links or files in order to get access to your network.
Malware Protection
Malware is a second approach by which attackers attempt to access your network. It is a wide phrase that includes a variety of dangerous software. This comprises viruses, trojans, worms, ransomware, spyware, adware, keyloggers, and others. According to our Ransomware Attacks study, one in every four (23.9%) IT professionals believes their organisation has been the target of a ransomware assault.
Endpoint Detection and Response (EDR) on end user devices, as well as rigors firewall rules and security solutions that prevent internal and external malicious activity, provide the greatest protection. You may learn more about malware assaults in Malware vs. Viruses: Understanding the Threat Landscape.
Poor security practices lead to data leaks
First and foremost, there is a catastrophic security culture. Your credentials are the first point of attack. Never use a weak password to secure your online accounts. If you are an IT administrator, you should implement a password policy to prohibit the usage of weak passwords. You may learn more in the next section.

When you log in with your account on a shared computer at work or in public, always log out. If you don’t and someone else, maybe a dangerous person, acquires access to your email, it might result in a data breach.
An absence of precaution might also be that someone mistakenly sent an email to the incorrect external email address (misdelivery). Even a second of inadvertent activity might cause serious issues for us.
This occurs when a person mistakenly sends sensitive information to the incorrect email address. According to the Verizon Data Breach Report 2022, there were 715 incidents, 708 of which resulted in confirmed data breaches, compromising personal, medical, financial, and other data.
Risks of Bad Password Management
IT staff are responsible for enforcing company password regulations. This largely comprises the usage of complicated passwords with lower and uppercase letters, digits, and special characters.
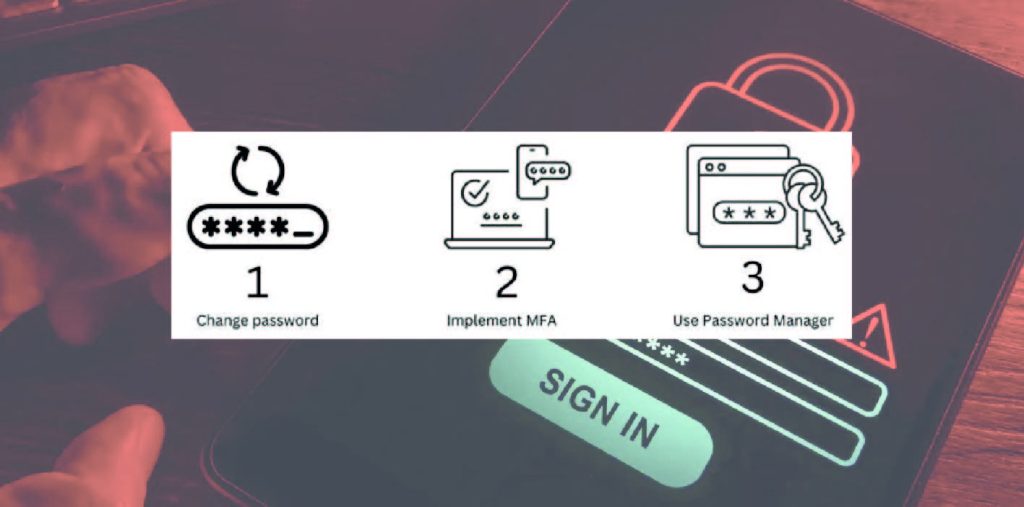
Various security solution vendors provide varying suggestions on how many characters a password should have. The basic guideline is that the more characters, the better. Do not use fewer than 12 characters.
You may also implement various password restrictions, such as lockout policies, deactivating inactive accounts, adding multi-factor authentication (MFA), measuring password strength, monitoring account access, implementing SSO, and so on.
The bottom line is that just using a username and password to identify a user is no longer sufficient; instead, if feasible, employ strong authentication such as MFA, especially phishing-resistant MFA such as FIDO 2 physical keys, or biometrics such as Windows Hello.
Implement Password Managers
Do not write your password on sticky notes, notes, or anyplace else. It is advisable to use a password manager and save your passwords in safe, encrypted vaults. When you require your password for a service or device, log into your password manager, copy it, and then enter it.
Password Managers additionally offers plugins for your favourite browsers that allow you to recover your password when you need to log in. This technique benefits users at all levels, from end users to IT administrators managing many platforms.
What Should I Do If I Find My Email Address in a Leak?
If you discover your email address in an email leak, you should immediately change your password. A new password should adhere to the preceding section’s guidelines.
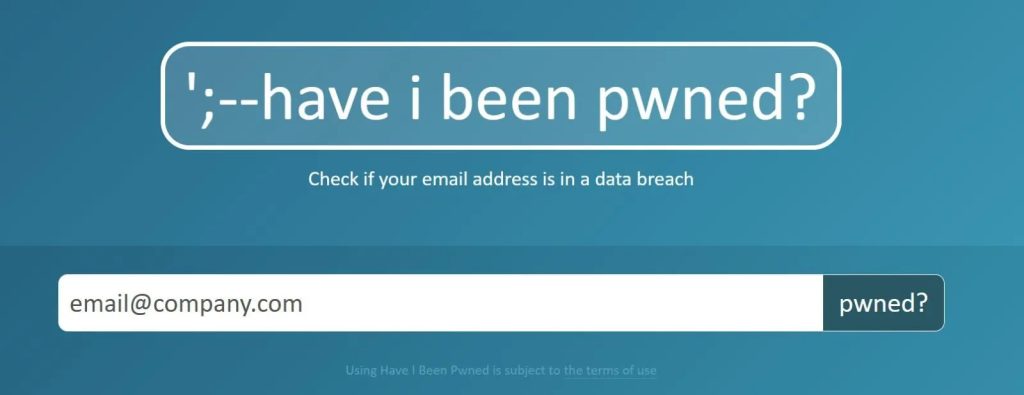
Use Password Managers to save your password; do not write or print it on paper, save it in.txt or other files on your computer, or send it over email. Password managers are meant to be as secure as possible.
In the event of an email leak in an organisation, you should notify all key stakeholders and investigate any suspicious activity on impacted services.
How to prevent data leakage doing Email security check in 2024
From an IT management standpoint, you should implement access control and specify who may do what. One of the most critical steps is to implement access control with minimal authorization.
Your data should be encrypted wherever it is kept, both in transit and in storage. Even if a bad individual has access to the data, they are unable to read it.
Security is shared responsibility. Make certain that your network and endpoints have adequate security protection in place, and that your workers have received data handling training. Furthermore, you should maintain continual monitoring and tracking of all activity that occur on your services, whether internally or externally.
Keep your infrastructure up to date at both the physical and application levels, and patch it with the most recent changes. If our systems are not patched with the most recent security upgrades, they offer a significant security risk that attackers can exploit to obtain access to our network.
How IT Company Can Help You Stay Protected Against Data Leaks
According to the World Economic Forum’s Global Risks Report 2023, human error accounts for 95% of all cyber security breaches. Malicious individuals (read: hackers) attempt to abuse human psychology through phishing and social engineering.
Prioritizing Email security check protects not just sensitive information, but also your company’s integrity and image. By establishing regular security processes and remaining watchful against emerging cyber threats, you may strengthen your defenses and reduce the chance of data breaches in 2024 and beyond. Remember, when it comes to email security, prevention is always preferable to cure.
1. Strengthen Your Passwords.
2. Only use reliable Wi-Fi networks.
3. Maximise Two-Factor Authentication (2FA) and Think Before Clicking.
4. Never reveal your password.
5. Install antivirus software.
6. Check Email Security and Privacy Settings.
1. Train your employees to be aware of cybersecurity risks.
2. Use Two-factor authentication (2FA).
3. Manage your passwords more effectively.
4. Be wary of phishing emails.
5. Encrypt the email.
6. Improve Endpoint and Email Security Hygiene.
7. Prevent data leaks and breaches.
8. Implement robust email defences.
1. Use Sender Authentication to protect your email accounts.
2. Lock spam and unwanted senders.
3. Be wary of attachments and avoid clicking links in emails.
4. Use strong passwords for email accounts and avoid reusing passwords.
5. Implement multi-factor authentication.
6. Keep your business and personal emails separate.
7. Avoid using public Wi-Fi.