
Table of Contents
ToggleIndustries and businesses rely significantly on technology for day-to-day operations as a result of digital transformation. With this reliance comes a greater danger of cyber assaults, which can have negative consequences if vulnerability scan service is not used.
Vulnerability scanning has become an essential component of cybersecurity to reduce these threats. Manual vulnerability scans, on the other hand, can be time-consuming, repetitive, and prone to human mistakes.
Automation has emerged as a significant answer to these difficulties. This article will look into:
- The advantages of automated vulnerability scanning
- Automation of vulnerability screening best practices
- How can automated vulnerability screening help enterprises improve their security posture?
What is the importance of vulnerability scanning?
Approximately 8,000 vulnerabilities were released in Q4 2023, and the National Vulnerability Database (NVD) currently contains approximately 176,000 vulnerability entities in its database. Given that 76% of apps contain at least one vulnerability, Vulnerability scanning is critical for businesses and organizations to maintain robust cybersecurity defenses.

Determine your Weak points
Vulnerability scanning assists in identifying gaps or vulnerabilities in the network, applications, and systems that attackers may use to obtain unwanted access.
Preventative Security
Data breaches in the third quarter of 2023 revealed nearly 15 million data records globally, a 37% increase from the first quarter. 3 Regular vulnerability scans enable firms to resolve vulnerabilities before attackers can exploit them, preventing data breaches.
Requirements for Compliance
To achieve compliance with security standards and laws, many sectors and regulatory agencies need frequent vulnerability scanning. Some examples of such compliance requirements include PCI-DSS.
What are the Types of Vulnerability Assessment Scanning?

1- Network-based Scans
This sort of vulnerability scanning focuses on discovering flaws in network infrastructure such as routers, switches, firewalls, and servers. It entails analyzing network devices for known vulnerabilities and configuration flaws that attackers might exploit.
2- Application Vulnerability Scanning
Application vulnerability scanning entails detecting flaws in software programs such as online applications, mobile apps, and desktop applications. It often entails automated testing of the application’s code and input fields for common vulnerabilities such as SQL injection, cross-site scripting (XSS), and buffer overflow.
3- Database Vulnerability Scanning
This sort of vulnerability assessment focuses on discovering flaws in database systems such as SQL servers and Oracle databases. It entails searching databases for known flaws and misconfigurations that attackers might exploit.
How do you Automate Vulnerability Scanning?
Using tools and technology to run vulnerability checks without manual involvement is what automation is all about. Here are several procedures for automating vulnerability scanning:
1- Select vulnerability scanners
The first and most important step in automating vulnerability detection is to select a vulnerability screening solution. There are several vulnerability scanning technologies on the market, including Nessus, Qualys, and OpenVAS. Choose an automated vulnerability scanner that fulfills the demands, budget, and technological constraints of your firm.
2-Specify scan targets
Determine which assets and systems require scanning. This might include servers, apps, network devices, or databases.
3-Schedule scans
Make a vulnerability scan service schedule. This might be done on a daily, weekly, or monthly basis, depending on the needs of the company. A more regular vulnerability screening schedule, with the use of automated technologies, might improve the odds of finding problems. However, daily or weekly scanning may not be essential for every company.
4-Configure scan settings
Configure the vulnerability scanner parameters, such as the types of vulnerabilities to check for, severity levels, and scan scope.
5-Automatic reporting
Configure the vulnerability scanner to create reports and warnings automatically when vulnerabilities are discovered. This will assist guarantee that you or the QA team is contacted and may take prompt action to address the vulnerabilities.
6-Combine with additional security technologies
Consider combining the vulnerability scanner with additional security tools, including as patch management systems and security information and event management (SIEM) solutions, to expedite vulnerability management.
Organizations may save labor, save time, and proactively find and repair vulnerabilities before attackers exploit them by automating vulnerability screening. This will assist enterprises in maintaining robust cybersecurity defenses and protecting themselves from cyber-attacks.
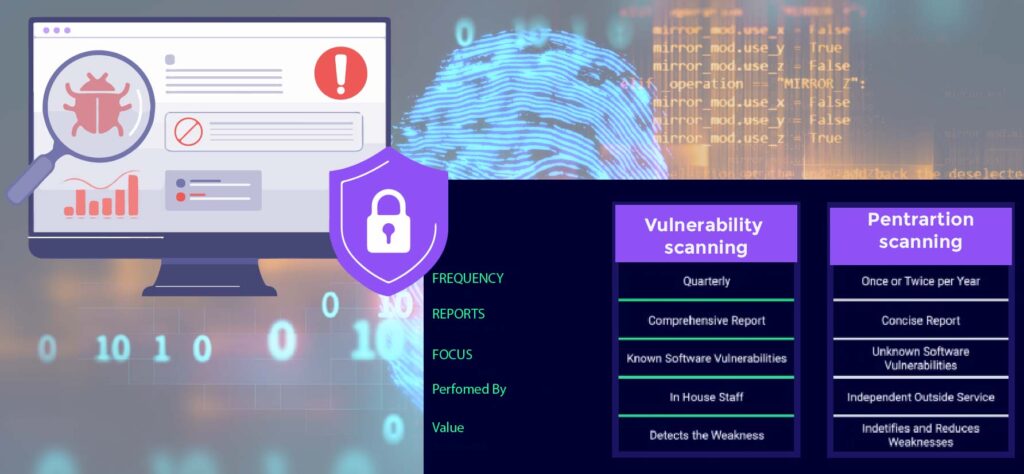
Wrapping Up
To summarize, implementing automated vulnerability scanning is not an option; it is a need for increasing digital security. Our cutting-edge Vulnerability Scan Service from IT company provides premier automation, providing solid security measures. Take command of your system’s security, streamline processes, and simply keep ahead of any risks. Increase your security posture with our dependable and creative solutions now. Trust us to protect your digital assets while you focus on growing your company.





