
Table of Contents
ToggleProtecting sensitive information sent via email in 2024 is nowadays highly important. As organizations increasingly rely on email as their major form of communication, implementing strong security measures is critical to preventing possible cyber attacks. Recently, Microsoft released an urgent security advisory emphasizing the CVE-2024-21413 code error vulnerability, which affects a variety of Microsoft products. IT Company Premium Email Security service provides innovative techniques to strengthen your defenses, reduce vulnerabilities, and protect your sensitive data.
Define your email security objectives and measurements
The first step in assessing your security posture is to establish goals and KPIs based on your company’s objectives, risk tolerance, regulatory needs, and industry standards. For example, you could track the percentage of incoming and outgoing emails encrypted, the number of instances. Having specific and quantifiable objectives and metrics will allow you to assess your existing security performance and find areas for improvement.
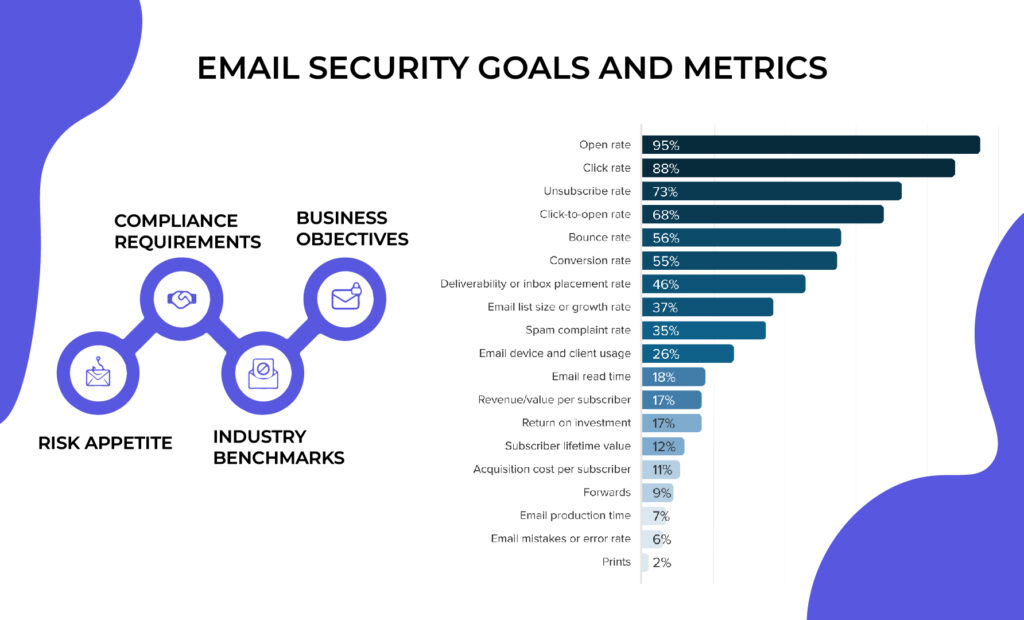
Email Security aims include preserving private information, preventing unwanted access, and maintaining communication integrity. Metrics include lower phishing click rates, better detection of harmful attachments, and faster incident response times. By establishing these objectives and benchmarks, an organization hopes to strengthen its email defenses, reduce security incidents, and develop a resilient cybersecurity posture in the face of emerging email threats.
Conduct a comprehensive email security audit
The next stage is to do a detailed audit, which entails analyzing your security policies, procedures, tools, and practices and comparing them to your objectives and metrics, as well as the best practices and standards in your sector and area. For example, you may want to ensure that your security policies are current and consistent.
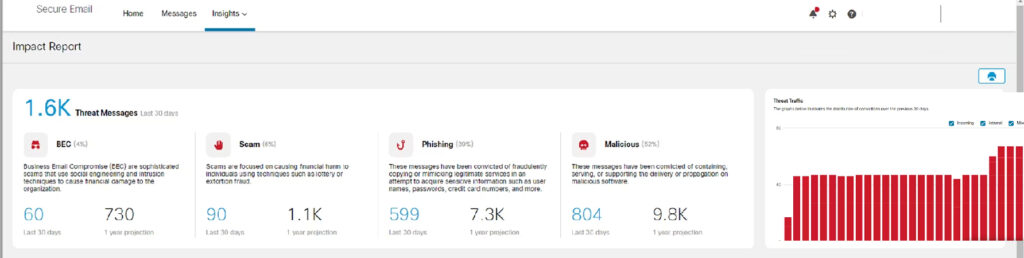
Security processes must be documented, and streamlined, and your tools are configured and updated. Make sure that security practices are consistent with the principle of least privilege, the defense-in-depth approach. A comprehensive Email Security audit can help you discover any loopholes or vulnerabilities.
Perform regular security testing and monitoring
The third stage is to do frequent security testing and monitoring, which includes modeling and evaluating various security threats, as well as gathering and assessing data and input from your systems and users. For example, you might run security tests like vulnerability scanning with website security tester and email security check.
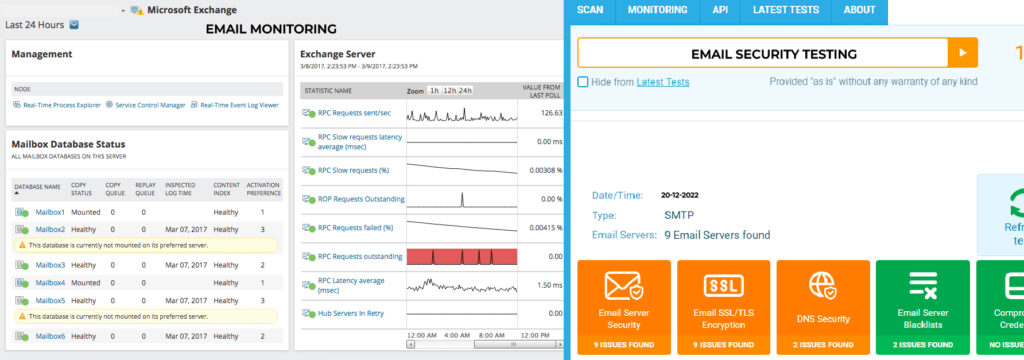
Companies can also track indicators like spam rate, malware detection rate, bounce rate, and user behavior. Regular testing and monitoring will assist you in validating your record and identifying any vulnerabilities or issues requiring improvements or analysis.
Implement email security best practices and recommendations
The fourth phase is the implementation of best practices and suggestions into action, which includes applying the lessons gained from your security audit, testing, and monitoring. For example, you could consider implementing security recommendations such as using secure passwords and two-factor authentication, enabling encrypted emails and electronic signatures.
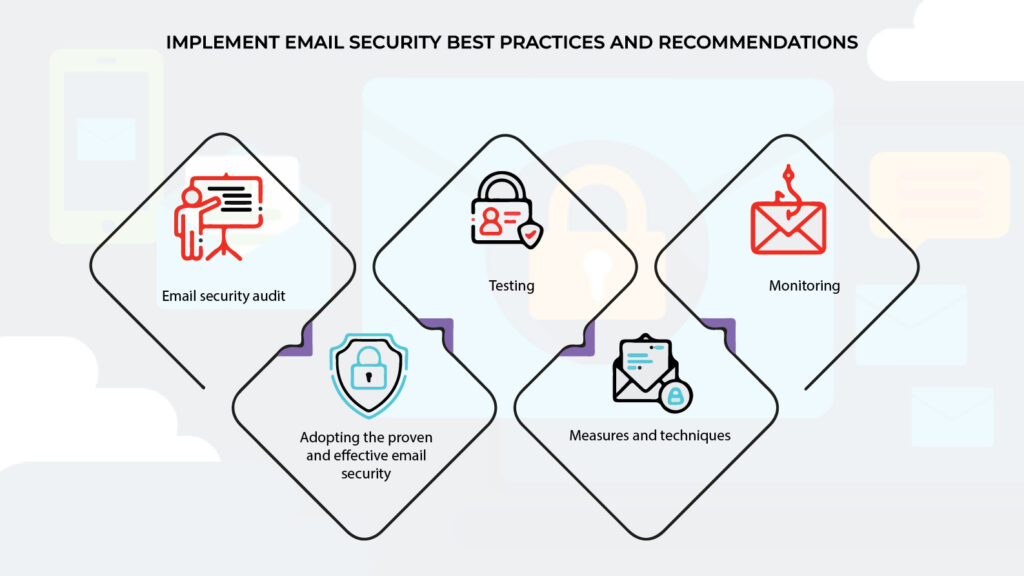
Implementing core protocols such as DKIM, SPF, and DMARC is critical for Email Security. Beyond this, it is critical to actively improve your security framework. This includes using MTA-STS and TLS-RPT to encrypt email content and integrating SMTP DANE to improve TLS connection security. DNSSEC is critical for preventing email misdirection to malicious servers. For complete protection, end-to-end encryption using PGP or S/MIME is required.
Review and Upgrade your Security level regularly
The third stage is to assess and update your Email Security by examining your goals and metrics, auditing, testing, monitoring, and making any required modifications or upgrades in response to the evolving security environment and threats.

For example, you may want to review and update on a regular basis based on stakeholder feedback, Security testing and monitoring results, the most recent security trends and innovations, emerging security threats and challenges, and evolving security regulations and standards. Regularly reviewing and upgrading your security level can help you sustain it and respond to the changing environment.
Conclusion
Finally, having strong security is critical in protecting your organization from cyber-attacks. Recent occurrences, such as Microsoft’s urgent Security Alert for CVE-2024-21413, highlight how vulnerabilities could be serious dangers to email systems. IT Company Premium Email Security offers full protection against emerging threats by setting security goals, conducting audits, testing regularly and following best practices.
The initial stage in doing a security audit is to identify possible threats and vulnerabilities. Start by examining your present security rules and processes, as well as any recent security issues. Consider both internal and external risks, including phishing, malware, illegal access, and data breaches. Consider the possible impact of these risks and vulnerabilities on your business operations and data.
Create an action plan to address the risks and vulnerabilities discovered by your security audit. Prioritize activities based on their possible influence on your business’s operations and data. Ensure that your action plan is in line with your budget, resources, and company objectives. Create a timeframe for implementation and allocate duties to the appropriate parties.





